Back in the days before Gmail, webmail on the Internet was really, really bad. Inboxes were limited to 10 or 20 megabytes, interfaces were slow and ugly, and the experience simply didn’t come close to matching what most desktop clients offered. This is how I remember Hotmail. I hated it. In fact, since signing up for Gmail in 2004, the only times I’ve checked out Microsoft’s webmail client were immediately after big launches, at which point I would reactivate my account, give it a quick run through, and promptly decide that it still wasn’t very good. So when I say that the new version of Hotmail that’s launching this summer has me excited, that’s saying something.
This morning, Microsoft showcased this new version of Hotmail to a room full of press at its offices in San Francisco. It’s fast, slick, and comes with a set of new features for managing large amounts of email that make it a much better rival to Gmail. Does it look like a revolution? Not really. But it does incorporate some very nice features — things that seem quite obvious once you seem them in action, but aren’t already available elsewhere. And more importantly, they’re features that regular people will actually use.
First, the stuff that Hotmail is really just playing catchup with. The first thing you’ll notice is that threaded conversations are now offered, and it looks like they’re the default (though you can turn them off). The search box now features auto complete. You can flag messages (I can’t believe this wasn’t available before). There’s better spam protection. Gmail users should stop yawning, because there’s plenty of other good stuff.
Perhaps the most important suite of features, at least to people who commonly experience inbox overload, are all the new filtering and message management tools the new Hotmail comes with. My favorite is called ‘Sweep’. If you’ve subscribed to a newsletter but decide you don’t want to filling up your inbox any more, you can hit activate this option to move every message you receive from that sender to a folder other than your mail inbox. Other webmail clients can do this too, but the flow for this looks easier than, say, making a filter in Gmail.
Another feature, called Hotmail Highlights, breaks out your messages according to where they’re coming from. One section shows you at a glance whether you’ve received any messages from people in your address book. Another shows you any messages you have from social networks like Facebook. On the left hand side of the screen, you’ll see a few options under the label “Quick View”. One of these is for photos — click it, and you’ll see all the messages in your inbox that have either image attachments or links to photo albums on sites like Flickr. There’s a similar option for Documents, as well as one that lets you immediately find shipping updates.
The other big features involve reading and composing messages. When you receive a message that has either photo attachments or links to an online photo album, Hotmail will use those photos to build a slick slideshow (it uses Silverlight). The service is even better for sending photos. Most email services aren’t great for sending photos, because they have a limit of 10-20 megabytes per message (and you also have to worry about whether the recipient’s service will allow for messages that large). Hotmail works around this by automatically uploading your images to Microsoft’s cloud storage service SkyDrive, which is free up to 25 GB. The resulting message looks great — Hotmail builds a photo album that should be visible in any mail client that supports rich formatting, and it doesn’t kill anyone’s inbox storage.
Finally there’s Hotmail’s integration with Microsoft’s online version of Office. When you receive a document in Hotmail, you have the option to view and edit it using the online versions of Office, and then save and send any changes back to the original sender. These online apps have strong integration with the desktop versions of Office 2010, but you don’t need the desktop apps in order to use the online versions for free. This is of course Microsoft’s answer to Google Docs, which is itself integrated into Gmail, and it looks well done (I expect document fidelity will be better for Microsoft, which may be a big sticking point).
I should point out that Yahoo Mail offers some of these features already (like the ability to break out messages that were sent by your contacts). And while Gmail doesn’t offer some of these features as part of its default set, you can reproduce some of them using filters. Hotmail doesn’t necessarily need to outdo its competitors in every respect — it’s still the largest email provider worldwide, with 360 million active accounts. But Gmail is growing fastest, and Microsoft is looking to curb that growth. This new launch probably isn’t going to spark any kind of mass migration away from Google’s services, it may well draw a few more former AOL users who are now looking for a new webmail provider.
Microsoft expects to ship the new Hotmail in mid-summer.
Read full story
This morning, Microsoft showcased this new version of Hotmail to a room full of press at its offices in San Francisco. It’s fast, slick, and comes with a set of new features for managing large amounts of email that make it a much better rival to Gmail. Does it look like a revolution? Not really. But it does incorporate some very nice features — things that seem quite obvious once you seem them in action, but aren’t already available elsewhere. And more importantly, they’re features that regular people will actually use.
First, the stuff that Hotmail is really just playing catchup with. The first thing you’ll notice is that threaded conversations are now offered, and it looks like they’re the default (though you can turn them off). The search box now features auto complete. You can flag messages (I can’t believe this wasn’t available before). There’s better spam protection. Gmail users should stop yawning, because there’s plenty of other good stuff.
Perhaps the most important suite of features, at least to people who commonly experience inbox overload, are all the new filtering and message management tools the new Hotmail comes with. My favorite is called ‘Sweep’. If you’ve subscribed to a newsletter but decide you don’t want to filling up your inbox any more, you can hit activate this option to move every message you receive from that sender to a folder other than your mail inbox. Other webmail clients can do this too, but the flow for this looks easier than, say, making a filter in Gmail.
Another feature, called Hotmail Highlights, breaks out your messages according to where they’re coming from. One section shows you at a glance whether you’ve received any messages from people in your address book. Another shows you any messages you have from social networks like Facebook. On the left hand side of the screen, you’ll see a few options under the label “Quick View”. One of these is for photos — click it, and you’ll see all the messages in your inbox that have either image attachments or links to photo albums on sites like Flickr. There’s a similar option for Documents, as well as one that lets you immediately find shipping updates.
The other big features involve reading and composing messages. When you receive a message that has either photo attachments or links to an online photo album, Hotmail will use those photos to build a slick slideshow (it uses Silverlight). The service is even better for sending photos. Most email services aren’t great for sending photos, because they have a limit of 10-20 megabytes per message (and you also have to worry about whether the recipient’s service will allow for messages that large). Hotmail works around this by automatically uploading your images to Microsoft’s cloud storage service SkyDrive, which is free up to 25 GB. The resulting message looks great — Hotmail builds a photo album that should be visible in any mail client that supports rich formatting, and it doesn’t kill anyone’s inbox storage.
Finally there’s Hotmail’s integration with Microsoft’s online version of Office. When you receive a document in Hotmail, you have the option to view and edit it using the online versions of Office, and then save and send any changes back to the original sender. These online apps have strong integration with the desktop versions of Office 2010, but you don’t need the desktop apps in order to use the online versions for free. This is of course Microsoft’s answer to Google Docs, which is itself integrated into Gmail, and it looks well done (I expect document fidelity will be better for Microsoft, which may be a big sticking point).
I should point out that Yahoo Mail offers some of these features already (like the ability to break out messages that were sent by your contacts). And while Gmail doesn’t offer some of these features as part of its default set, you can reproduce some of them using filters. Hotmail doesn’t necessarily need to outdo its competitors in every respect — it’s still the largest email provider worldwide, with 360 million active accounts. But Gmail is growing fastest, and Microsoft is looking to curb that growth. This new launch probably isn’t going to spark any kind of mass migration away from Google’s services, it may well draw a few more former AOL users who are now looking for a new webmail provider.
Microsoft expects to ship the new Hotmail in mid-summer.

























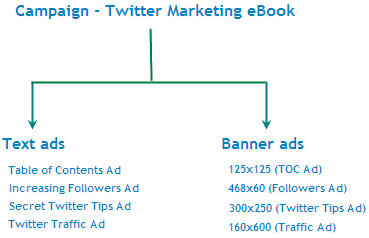
 Twitter is a social network and microblogging website that allows its members to post and read messages known as tweets. Twitter helps people to communicate and stay connected through the trade of rapid, frequent, 140 character messages or tweets. Tweets are text-based content displayed in the author's account page and brought to the writer's subscribers who're called followers. Twitter's aim is actually to give a service that enables individuals to discover and have content from sources which get your interest as well as to talk about your content material with other people.
Twitter is a social network and microblogging website that allows its members to post and read messages known as tweets. Twitter helps people to communicate and stay connected through the trade of rapid, frequent, 140 character messages or tweets. Tweets are text-based content displayed in the author's account page and brought to the writer's subscribers who're called followers. Twitter's aim is actually to give a service that enables individuals to discover and have content from sources which get your interest as well as to talk about your content material with other people.
 Pop up ads are of three different categories namely pop-ups created by spyware and adware, messengers service advertisement and general browser pop-ups. Pop-ups ads occasionally appear on the screen and interfere with the user's ability to view the contents displayed on the screen. The user can easily avoid these advertisements by installing a pop-up blocker.
Pop up ads are of three different categories namely pop-ups created by spyware and adware, messengers service advertisement and general browser pop-ups. Pop-ups ads occasionally appear on the screen and interfere with the user's ability to view the contents displayed on the screen. The user can easily avoid these advertisements by installing a pop-up blocker.



 Label cloud is a label or category that looks like a cloud. Actually, bloggers are provide labels cloud, but the label cloud from this blogger just by writing just one color. Label cloud that we will modify is how to make the writing colorful large and small as writing.
Label cloud is a label or category that looks like a cloud. Actually, bloggers are provide labels cloud, but the label cloud from this blogger just by writing just one color. Label cloud that we will modify is how to make the writing colorful large and small as writing.